How Does the Grok Token Exploiter Exploit the X Token By Baking His Own Cake And Eating it?
Strategy One Liner
The bot utilizes the methods of the ERC20 X token to create the arbitrage opportunity between a Uniswap V2 pool and a Uniswap V3 pool, and takes advantage of it, making a profit of $4,844.
Big Picture
EigenTX Link: https://bit.ly/3xMOYIt

Key Steps
Stage 1: Prep the Uniswap V2 X-WETH pool.
Step 0: Borrow 6,493,128,478.6032 X from the Uniswap V3 pool of X-WETH.

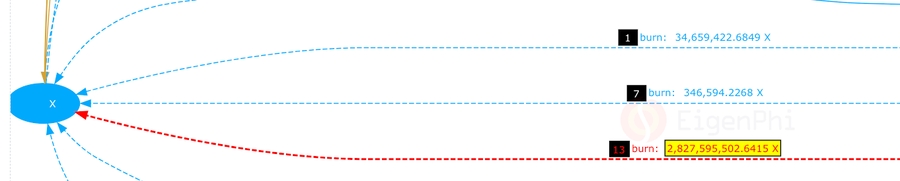
Steps 1-6: Swap 3,431,282,845.8058 X for 23.4081 ETH at UNI-V2, and transfer 34,659,422.6849 X back to X contract as a 1% tax.

Steps 7-12: Swap 34,312,828.4581 X for 0.2006 ETH at UNI-V2, transfer 346,594.2268 X back to X contract as a 1% tax.

Stage 2: Overflow the X contract to create the arbitrage prospect.
Step 13: Transfer 2,827,595,502.6415 X back to the X contract, bringing the balance of the X token of the X contract to 10,000,346,595.226849.
The simulation on Blocksec shows the effect.




Steps 14-26: Swap 99,000,000 X for 0.2892 ETH at UNI-V2, and transfer 1,000,000 X back to X contract as a 1% tax.
The swapping of X for ETH this time triggers an internal function, X.shouldContractSwap(), returning true, which is the result of the code below:
The transfer in step 13 satisfies the condition: the balance of X is bigger than the threshold of 10,000,000,000. Before step 13, this code returns False.
You can find it in the contract of the X token.

Next, the X contract injects 10,000,000,000 X tokens into the Uniswap V2 pool and puts the received ETH to its deployer’s EOA.
This huge injection of X inflates its value, causing the exchange rate of X against ETH to surge to 342,323,651 X per ETH. The price gap between this Uniswap V2 pool of X-ETH and the Uniswap V3 pool of X-WETH.
We can split the steps of 14 to 26 as below.
Steps 14-18: X contract transfer 10,000,000,000 X to UNI-V2 and swap X for 41.3756 WETH, unwrap WETH and transfer ETH back to X

Steps 19-20: X contract transfer 20.4830 ETH and 20.9020 ETH to an EOA address

Steps 21-26: To address finishes the swap operation at Uniswap V2 pool and pays tax.

Stage 3: Harness arbitrages.
Step 33: To address repays the flash loan, 6,558,059,763.3892 X, to the Uniswap V3 pool of X-WETH.

Steps 34-39: To address swaps 31,457,966.2838 X for 0.1402 ETH at the Uniswap V2 pool, transferring 317,757.2352 X back to X contract as a 1% tax.

Step 40: Borrow 5.1598 WETH from a new Uniswap V3 Pool of USDC-ETH.

Steps 41-48: To address swap 5.3 ETH for 1,123,530,803.0087 X at the Uniswap V2 pool, which transfers 11,348,795.99 X back to X contract as a 1% tax.


Steps 49-50: Swap 1,123,530,803.0087 X for 7.8274 WETH at the Uniswap V3 pool of X-WETH.

Step 51: To address repay the flashloan, 5.1624 WETH, to the second UniswapV3Pool.

Steps 52-53: Unwrap 2.6651 WETH to 2.6651 ETH.

Key Assets
X, ETH, WETH
Simplified Illustration

More Details
From the contract page on Etherscan, we can see the EOA labeled as GROK Toekn Exploiter did all the transactions.

2 transactions involving SPIKE utilized the same strategy to do arbitrages. You can find more details here.
Last updated
Was this helpful?